Password Format: Color-Country-Fruit
Hash: 17fbf5b2585f6aab45023af5f5250ac3
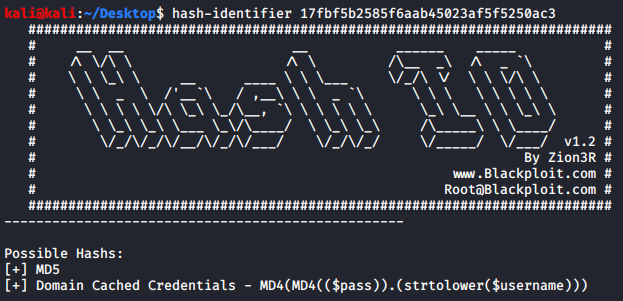
By analyzing the information provided we realized that the hash is probably a MD5 one because it is 32 characters long and hex-encoded.
Using hash-identifier on Kali Linux returns the same result:
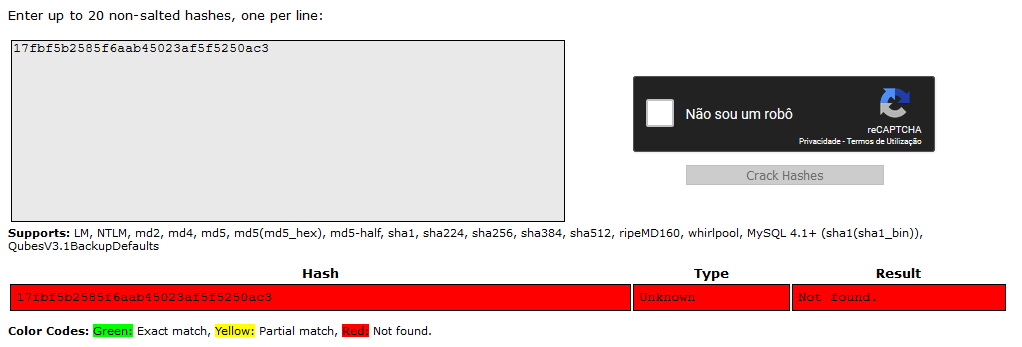
The first thing we tried was a rainbow table attack where we compared the hash with pre-computed hashes to see if there is a match.
However, this type of attack failed:
So, we moved on and decided to brute-force the password.
We downloaded some wordlists containing a bunch of color, country and fruit names.
Here are the links to them:
Then we converted every word in those files to the title format, which means that the first letter of the words will be capitalized. You can use a website like ConvertCase to achieve that.
We also built a Python program to concatenate the words together using the format given (Color-Country-Fruit), create a MD5 hash using the string and then compare it to the given hash:
import hashlib
for color in open("colors.txt", "r"):
color = color.strip()
for country in open("countries.txt", "r"):
country = country.strip()
for fruit in open("fruit.txt", "r"):
fruit = fruit.strip()
passwd = "{}-{}-{}".format(color, country, fruit)
passwd_hash = hashlib.md5(passwd.encode()).hexdigest()
if (passwd_hash == "17fbf5b2585f6aab45023af5f5250ac3"):
print(passwd)
If there is a match, we print the password to the screen. Simple as that:
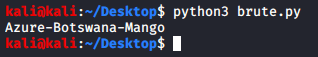
That way we could determine the password and, consequently, the flag.
This challenge was solved by my team, ducks0ci3ty.